In the last post we have seen the basic working principle of https. We have also seen that http is not secure and can be easily intercepted on a network. So the basic question that arises here is: Is https secure? We know that facebook or gmail provides the https connection automatically but are you sure that you are secure whenever you are browsing these https enabled websites? Well the truth is you're not. You may be thinking that these websites provide a secure connection and that you dont have to worry about security. But that's not true. You have to manually make sure, each time, that you're using an https connection. This is extremely important if you are on a public network. Well, we are going to see why.
What can an attacker do? Well, he cannot crack the encryption key so easily. But he can still get around the https. Basically if the user is not using a bookmarked https page to begin with, he is vulnerable to this form of attack. The underlying problem is that many a times the connection is started as an http connection. When you type facebook.com in the address bar, you are actually starting an http connection with facebook.com. The site then redirects you to an https page. However, an attacker, who is suitably placed between you and facebook.com, can modify this https redirection into an http redirection. The victim's browser will not show any certificate problems since it is connecting with an 'http' site. At the same time the attacker can start an https connection with the server and can use the credentials supplied by the victim to start his own https session with the server.
For this tutorial I have set up a virtual machine of backtrack linux on a Windows host. Note that the network adapter is in the bridged mode so that the two OSes work exactly like two different physical devices. You can use your favorite distro, we will be using the tools called sslstrip,arpspoof(comes with dsniff) and tcpdump.
First,we forward all the incoming packets on port 80(http port) to port 10000. 10000 will be the default port sslstrip will listen on.
Now we launch sslstrip using this command and keep the terminal open:
sslstrip.py
Now we will enable ip_forwarding.This is important because you need to forward the packets once you do an arp poisoning, otherwise it will become a denial of service attack. Open another terminal and use the command below:
Now we need to search for victims.You can scan the entire network using nmap.
The command used is:
nmap -PR 192.168.0.0/24
This will scan for the devices on my network with ip 192.168.0.0 (if you don't know your network ip, use the ifconfig command)
Here you can see the ip of my windows host. This was the output I obtained with the ipconfig command on Windows(just for a confirmation).
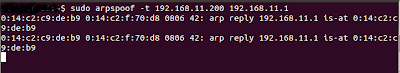
Now let's poison the victim with arpspoof. Issue the following command and keep the terminal open:
Here eth0 is my interface since its on a virtual machine (usually wlan0 for a wireless interface. Again, use ifconfig if you don't know your interface). 192.168.0.1 is the ip of the gateway.Usually the last byte is a 1.
Now all the packets the victim sends and receives will be routed through my machine. Now all I need to do is filter the traffic.Here I've used tcpdump. The command here filters the whole traffic for facebook login credentials. Open a terminal and use this command (keep the terminal open to capture passwords):
tcpdump -i eth0 host "www.facebook.com" -A|grep "&email="
Using wireshark to capture post data will be handy if you want to write filters of your own.
Now when www.facebook.com is opened from the host computer you can see an http login page instead of an https page.
Now give the credentials there and try logging in.
On going back to Virtualbox and examining the tcpdump capture, you can see the magic.
What you can do to avoid this situation is type in "https://www.facebook.com" instead of www.facebook.com. Another thing you can do is to keep the "https" page of facebook.com bookmarked and use it. That's it. Hope you've all understood why I told you to always make sure that you're using an https connection.
tags:-mitm, lan, against, https, sites, arp, poisoning, using, sslstrip, hack, facebook, public, network, use, backtrack